The security of company’s confidential data and employee’s personal information cannot be compromised at any cost but sharing the information within defined boundaries through a network is also necessary to put the information to use.
However, with the advancement in Information and Technology, networks today are getting more secured with the use of advanced network security technologies. Following are few network security technologies.
Highlights of Contents
1. 802.1X/RADIUS
It is a type of network security that provides authentication to both wired and wireless networks. This technology is mostly used in high security organizations and huge businesses. The installation and maintenance of this security system requires high levels of network security expertise. RADIUS is often employed to work with WPA/WPA2 – Enterprise encryption.
2. Wi-Fi Protected Access (WPA/WPA2)
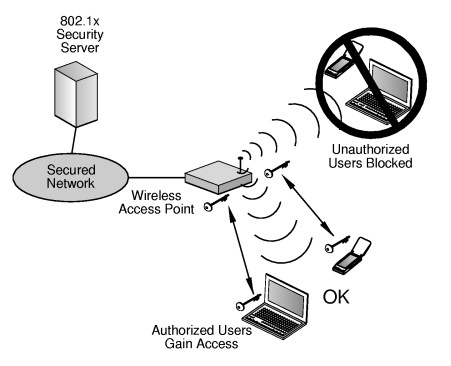
WPA is designed for personal or home wireless networks, whereas, WPA2 or WPA-Enterprise is used for small businesses and enterprises.
3. Wired Equivalent Privacy (WEP)
It is the standard security technology for Wi-Fi networks. It comes in different versions like WEP-40, WEP-104. It provides limited amount of security and can be used for home networks.
4. Network Data Encryption
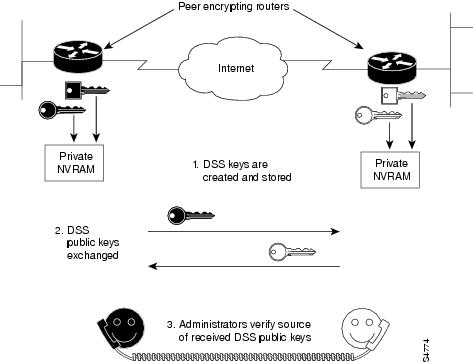
The most common and old, yet one method that is still very effective is data encryption. Most network security technology uses data encryption. It is scrambling of data sent over a network to hide from humans while the computer can still understand it clearly.
5. Host Based Encryption
It is optimal for networks working on a low bandwidth. Most E-commerce and e-mail transactions use a host-based encryption method. It is mostly software based and therefore limited by computer configurations.
6. Network Layer Firewalling VPN Technologies

It provides hiding of end-station addresses but the drawback is that it uses no data encryption. Usage of firewalling technology with or without network address translation is great for access control.
7. IP-SEC Based Security
It is a network layer security and can be integrated in a router. This technology is best for networks with wide array of links like ATMs, Dial up modems and frame relays.
8. Honey Pots
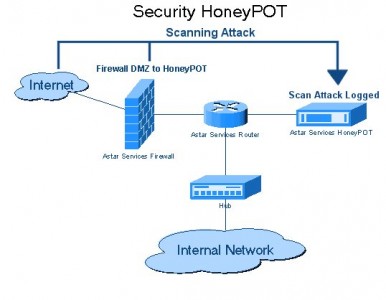
As the name suggests, these are computers set as bate for hackers, these are intentionally left vulnerable. When an intrusion is detected the hacker is caught or the gaping holes are identified and patched.
9. Access Authorization
Authorization mechanisms can vary from passwords, swipe cards or biometric recognition systems. Each user is provided with a means to access the network.
10. Link Layer Security System
These are normally found in VPN security gateways. Such gateways are found at the point-of-presence of WANs. Therefore it provides isolation between LAN and unsecured WANs.
Author Bio: John Clarkson is a Marketing Lead at Velocity Technology Partners. Velocity Technology Partners are leading Computer and IT Consultants. Services provided are Outsourcing IT, Healthcare IT support, Computer Networking, Managed IT Support, Cloud Based Services and Virtualization.
